The consolidation of middle- and back-office outsourcing is gaining popularity across the investment management industry. To date, there have been many debates around the pros and cons of this trend. Whether your firm has already made the decision to outsource or is actively evaluating options, there’s much to consider. How do you know you’ve made the right choice? Have you considered the most important factors? We believe wearing a “special” lens might reveal insights missing in existing discussions, paving the way for a novel method to assess comparable offerings and potentially result in superior outcomes.
This paper describes the framework for outsourcing in three stages. First, we present a quick history of outsourcing and its specific waves within the asset management industry. Second, we detail aspects overlooked in existing approaches. Finally, we describe a new model that could result in different, yet superior outcomes.
STAGE 1 – LOOKING BACK
“The longer you can look back, the farther forward you can see” – Winston Churchill.
Generic outsourcing
The act of outsourcing, in a broad context, has been happening for centuries. Ever since the advent of the industrial revolution when the concept of suppliers came into existence, outsourcing has been ingrained in economies. Production inputs provided by suppliers as raw material were procured from partners or monopolies. Moving finished goods to the final point of sale by distributors is a form of outsourced logistics.
In order to understand the distinctive nature of outsourcing manifesting today in asset management, let us consider the historical waves that exhibited since the late 1980s. From this point forward, technological innovations started to define business models. Investigating the causes of crests and troughs with the benefit of hindsight could lead to informed perspectives.
Outsourcing waves in asset management
The first outsourcing wave can be thought of as the age of automation that occurred in the final decades of the second millennium. It led to farming out of non-core processes. What started with one application slowly led to the service provider owning the entire technology stack deemed as non-value-adding functions. During this period, specific types of applications were outsourced that had simple business rules and were common across firms. A good example of this is custody position reconciliations.
The second outsourcing wave started with the recovery after the dot-com crash and outsourced a collection of distinct – but related – processes giving rise to the age of integrated automation. Having built their competence around multiple applications, outsourcing vendors gained subject matter expertise to handle the entire function. Extending the previous example, the entire reconciliation department consisting of position, cash and trade reconciliations was outsourced. By building bridges with brokers and custodians, service providers began to provide three-way reconciliations as a service.
Middle and back offices were always thought of as cost centers to an asset management firm, and there were pieces of them being outsourced in the first and second waves. The third outsourcing wave occurring now is much bigger in scale. It refers to completely outsourcing ALL processes in middle and back offices. For example, it means that position maintenance, street-side reconciliation, accounting, collateral management, and performance* are all collectively outsourced.
*Middle- and back-office functions comprise a much bigger list. Only a few are mentioned here.
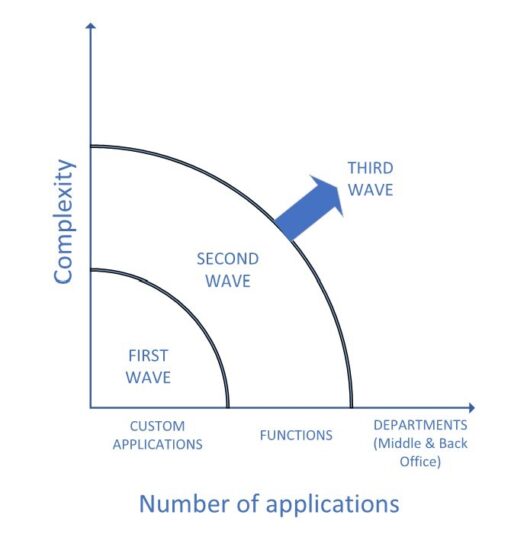
FIGURE 1: OUTSOURCING WAVES
Source: Meradia
Why is it happening now?
Previously, completely outsourcing middle- and back-office departments was a difficult task due to the level of extreme integration and high complexity. It might be apt to refer to the current times as “the ascending age of crystallizing competence.” A natural progression from technology to outsourcing entire business functions and departments has prompted firms to crystallize their core competence. Squeezing fee compressions makes asset management firms redeploy their people and resources towards their core objective of devising strategies and managing portfolios.
Technological disruption and nimbleness brought forward by cloud architectures are in stark contrast to the monolithic legacy systems in many firms. A rapidly evolving technological landscape poses the following question to asset management firms: “Should we be in the business of constantly upgrading our technology infrastructure and skills or is it best to procure them from the market?”
If the front office drives revenue, can middle and back offices be purchased?
STAGE 2 – STATUS QUO
There are many consolidated middle- and back-office outsourcing options in the marketplace today. Some service providers are large custodians, while others are software vendors. In addition, there is a curious mix of firms tying up with software vendors. With such a complex set of options, how does a firm choose? Conventional approaches usually involve shortlisting a handful of vendors who are eligible to participate in the selection process. Then, an RFP is issued and detailed responses are collected from the service providers. Finally, a sophisticated scoring mechanism follows to identify the top-rated vendor.
While this process collects enough information about the vendor and their service offerings, there are two commonly overlooked aspects:
- Risks – Even though a service provider could check all the boxes on functionality, several risks lie beneath the surface. These risks markedly determine the possibility of the RFP responses turning into a reality. Broadly, these fall into two types.
- Business risks that arise from change in the service provider’s macro-economic environment and strategy. These risks are external when viewed from the outsourcing firm’s perspective. However, that does not mean controls cannot be exercised. For example, a service provider who has been shortlisted for the final line-up has acquired another firm with compliance and ESG capabilities. While ESG is a valuable and new addition to the service provider’s offering list, compliance features overlap heavily. What would be the future plan? A best-of-breed approach raises questions around fitment and integration.
- Operational risks that stem from modified capabilities in the new model. Introducing new architecture and revised target operating models might result in newer capabilities not previously available. But, have existing service levels been compromised in any way? This does not discourage change and evolution. However, planning and thorough due diligence will reveal gaps that need to be addressed. Let’s say, for example, that a service provider agreed to deliver exposure-based futures returns. If a client were to question the validity of the return, this would require multiple back-and-forth conversations with the service provider to reveal calculation details and the underlying data. Lack of instant access to underlying information hinders quick research. What was once readily available within an in-house system may involve elapsed time in the service provider’s model. This issue is exacerbated when the asset management firm has tight SLA’s with its clients.
- Platform evaluation (Lessons from history)
- Enterprise Resource Planning (ERP) systems – initially deployed within manufacturing firms and quickly adopted by other industries – are more than just software. They offer unique and arguably efficient ways of illustrating how various processes should be executed. ERP systems operate in tight integration and are detached from day-to-day demands which could be ideal in some instances. But for a firm entrenched with unique ways of performing a business function, this might not bode well. The scars resulting from huge ERP investments have not gone away, including sunk costs.
- In many ways, consolidated middle- and back-office platforms of today are akin to ERP packages. These offer new or different ways to perform various processes. An efficient middle-and back-office solution, in total, has a lot of assumptions behind it, which may or may not be true based on how your firm works. For many firms with long-standing processes in place, understanding these new ways of working might seem a bit daunting, to put it mildly.
If risks are present, shouldn’t there be mitigation mechanisms?
STAGE 3 – THE NEW NORMAL
In this section, we describe key aspects of a framework that could alleviate the above concerns.
Total Risk Estimator (TRE)
Although cost is a major factor while evaluating most business decisions, the value delivered by an outsourcing provider is increasingly being requested in RFP documents. Many firms utilize a value/cost ratio to evaluate alternatives.
Total cost of ownership estimators are provided by many consulting firms that promise anticipated savings. It is an important, but small first step. This traditional metric shows potential benefits and touches upon risks but doesn’t offer the full picture. Optimistic estimations and overlooked factors fail to reveal the true scope and impact of the outsourcing decision.
We believe a total risk estimator (TRE) will add an important perspective to decision-making.
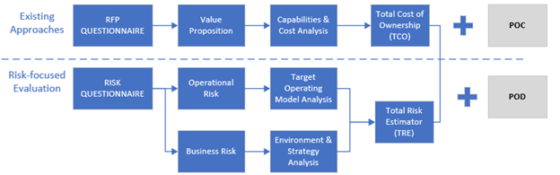
FIGURE 2: A RISK-BASED FRAMEWORK
Source: Meradia
Business risks
Could we realistically estimate future business risks for middle-and back-office outsourcing? Scenario-based risk estimation models are constantly deployed to measure and evaluate ex-ante risks within portfolio management. Modeling future business risks with related factors and parameters will help us refine our understanding of specific conditions. Here are some examples:
- Does the service provider’s claim change on acquiring or getting acquired by another firm? While synergies are expected to provide increased benefits, do risks amplify?
- Often, a pipeline of enhancements is shown as a response to meet requirements that aren’t supported yet. What factors impede that progress?
- Can you work hand in glove with the service provider to offset some of those risks?
A possible mitigation plan through analysis of the service provider’s environment and strategy: Visibility into the enhancement pipeline will reveal certain aspects of the platform’s future strategy. Juxtaposing this with key trends from close competitors could help benchmark the service provider’s future path. Knowledge of competing service providers plays a pivotal role in this regard.
Operational risks
- What are the training requirements and expectations? This is bi-directional. Client to service provider on the firm’s processes; Service provider to client on platform features and delivery service levels.
- Can the service provider adhere to all requisite regulatory guidelines?
- What mechanisms are in place to support rerun requests? What does the future operating model have in store?
A possible mitigation response by analyzing aspects of the target operating model: In the current model, an operations user could manually trigger the amortization process in an in-house system. In case a service provider’s platform is inaccessible or unable to rerun the process, establish required steps and identify the lead time. Then, revise policies and manuals as necessary.
Each risk identified above would be tagged along three dimensions – likelihood of occurrence, the magnitude of impact and confidence of mitigation mechanism. Tabulated individual risk scores would be weighted based on client preferences to yield a total risk estimate.
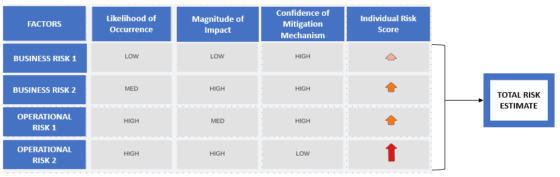
FIGURE 3: TOTAL RISK ESTIMATOR MODEL
Source: Meradia
Return maximization is seldom achieved without properly defined risk mitigation mechanisms.
Proof of delivery (POD)
Joseph Schumpeter coined the term “creative destruction” in 1942 [1]. It was used to describe disruptive technologies that significantly raise productivity. He said that while an evolutionary process rewards both improvements and innovations, it also pushes less efficient ways of doing work to the wayside. Schumpeter’s term started receiving attention again in the past decade when firms with technologically superior capabilities devised new business models to gain significant market share.
In the digitized era, evaluating the platform is paramount. A service provider who has the most innovative solution might quickly drive out competing rivals. Your chosen outsourcing provider might very well possess the next superior middle- and back-office platform. Alternatively, they may fail to deliver on that fantastic vision. A thorough dissection of the platform through informed use cases and subsequent benchmarking to industry best practices is of paramount importance.
Remember: Platform capabilities drive service levels, and not the other way around. Assuming we look deep into the platform, what could your firm gain?
- Perspective: Take the time to internally evaluate the service provider’s claim. You understand your firm’s needs better than anyone else.
- Capabilities: Understand the flexibility of the platform.
- Certainty: Increase confidence in an otherwise fluid environment where technology changes are happening rapidly, and scalability concerns are paramount.
A traditional proof of concept (POC) approach to evaluating the platform misses a couple of important aspects:
- It focuses on how the functionality works, but not with your data.
- It suggests the required analytics can be calculated but fails to reveal how they can be accessed.
Hence, a natural extension of POC – a Proof of Delivery (POD) – is more effective to evaluate data and workflow before the deal is inked. Risk items that received a high score from a target operating model standpoint in the above assessment could help identify important use cases. A POD will entail providing trades, confirmations and required reference information to service providers on a handful of accounts to accommodate a targeted set of use cases. Holdings, cash balance, performance and risk analytics info generated in totality by the service provider can be examined for correctness and completeness.
Typical POC vs POD
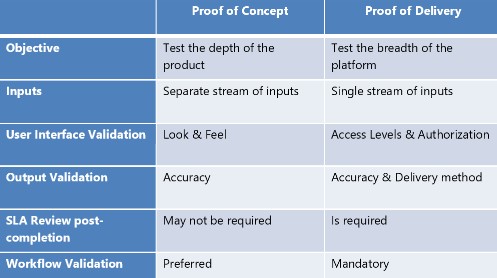
Too often, the focus is expended on functionality. Superior functionality that cannot deliver data seamlessly is of less value to you. The underlying platform should be evaluated in tandem with workflow capabilities and service delivery levels.
Concluding remarks
Outsourcing has provided significant benefits to the investment industry at large, but not without hiccups. The current wave is much bigger in scale and complexity. Firms would be amiss if they failed to do an accurate risk assessment leveraging lessons from history.
We hope this article helps investment management firms to commence educated conversations with service providers. However, this is just the tip of the iceberg. Proper establishment of risk mitigation mechanisms and precise definition of the future operating model will ultimately determine which side of the outsourcing fence you would land on.
If we were to adopt Churchill’s remarks to our industry, we would say, “The farther backward (lessons from outsourcing history) and inward (risk analysis and platform dissection) you look, the farther forward (alignment) you are likely to see.”
HOW MERADIA CAN HELP
The decision to outsource is multi-faceted, and what works for one investment management firm may not work for another. Meradia has a deep understanding of the landscape and can help you navigate the path to outsourcing.
[1] Joseph Alois Schumpeter. “Capitalism, Socialism, and Democracy,” 1942.
Download Thought Leadership Article Investment Accounting, Performance, Risk & Analytics Asset Managers, Service Providers & Outsourcers Jose Michaelraj info@meradia.com
info@meradia.com


